If they says they don’t know your password, how can they tell you not to use a previous password?
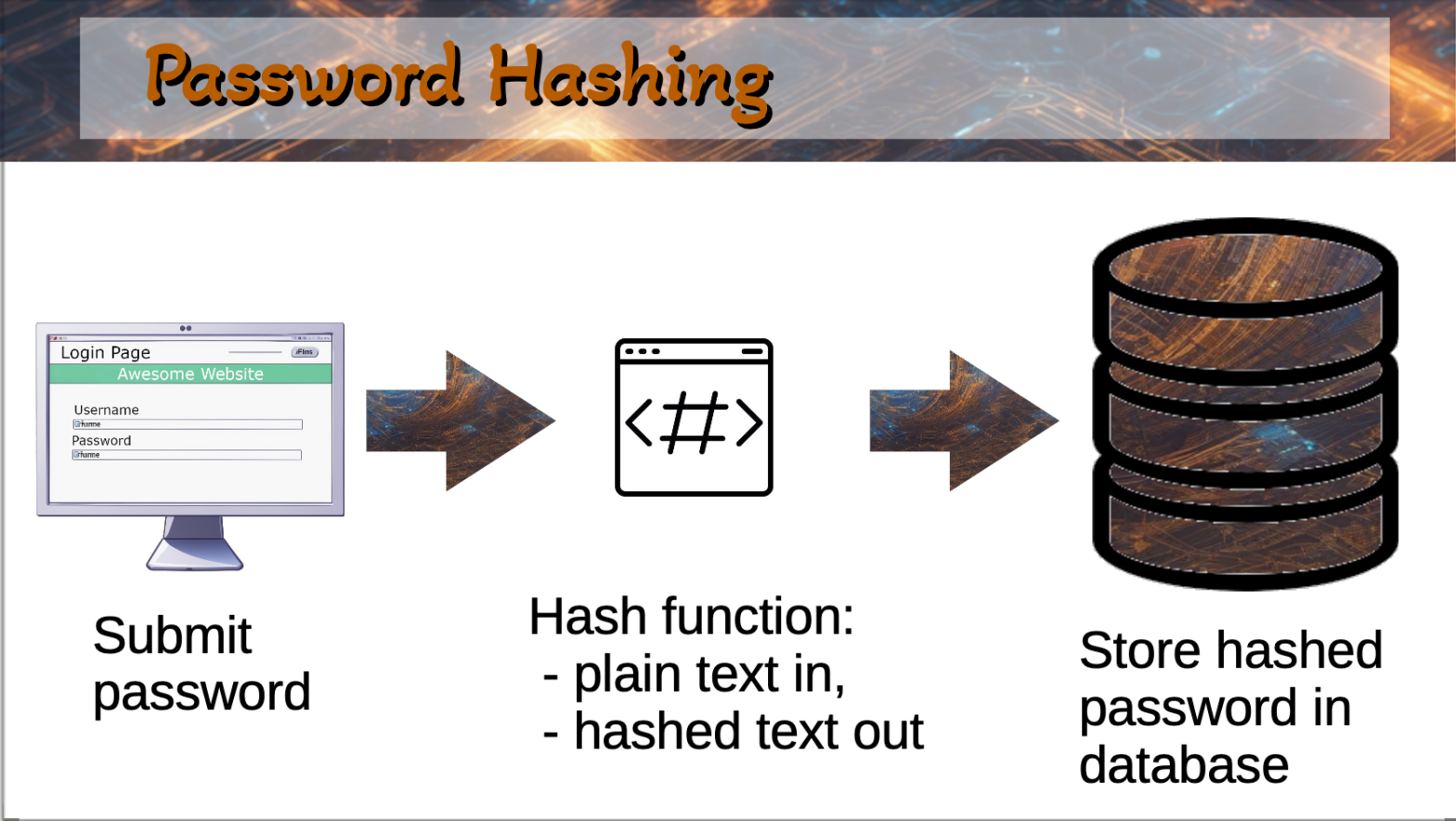
Your password should NEVER be stored in plain text in the database. They should only ever store a hashed version of your password.
How does hashing work?
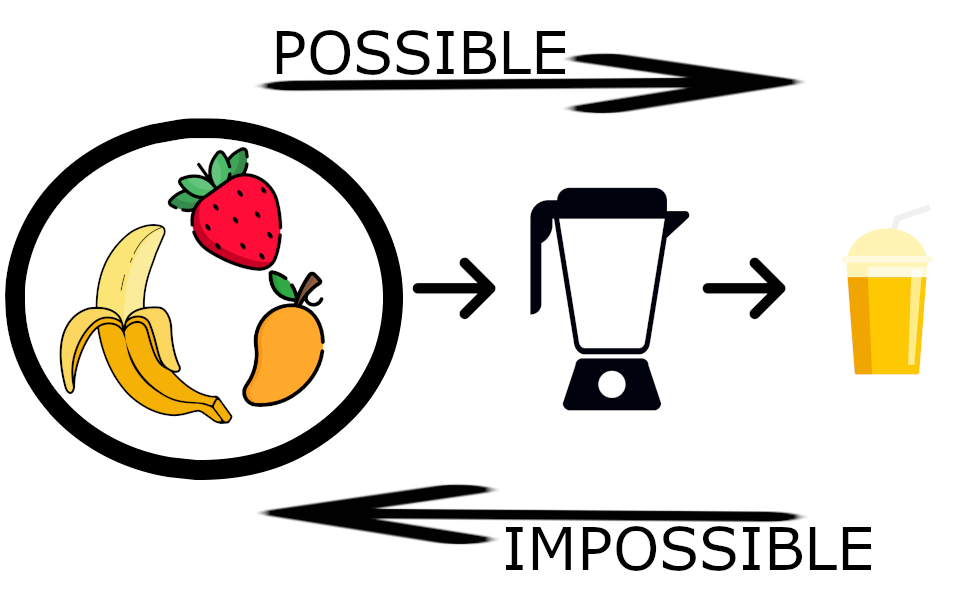
How is this hashed password achieved? By running your password through a hashing algorithm. A hashing algorithm is a mathematical function that produces text that looks nothing like your password. This hashed value is what is stored in the database, as it cannot be reversed to obtain your password.
Hashing algorithms produce values that are deterministic, which means that the same input always produces the same output. Therefore, every time the user logs in, the password they supply, is put through the same hashing algorithm. The system then verifies that the hash it just calculated, is the same as the hash that is stored in the database. If it matches, the user entered the correct password.
Similarly, when the user changes their password, the code simply runs their newly suggested password through the same hashing algorithm. If the hashed value of the new password is the same as the hashed value of the old password, then they can deduce that the user entered a password that was previously used. This is all done without the company ever actually knowing your password.
How does this apply?
What does this mean to you? If you ever contact a help desk or system administrator and they are able to “help” you and tell you what your forgotten password is, run a mile. It means they are storing your password in plain text – a severe security vulnerability. I would stop using that app. Furthermore, if you reused the compromised password on other apps, I recommend changing those passwords too. It is a good idea to not reuse passwords in the future.
I myself have had an admin tell me my password for a particular piece of software and it was most unsettling.
Further Reading
https://developer.okta.com/blog/2019/07/29/hashing-techniques-for-password-storage
https://auth0.com/blog/hashing-passwords-one-way-road-to-security/